Introduction
Alternate Data Streams (ADS) allow arbitrary metadata to be associated with files and directories on Windows NTFS. Alternate data streams are the Windows implementation of forks. The apparent size of the file will be unchanged, and most applications and users are unaware of their existence. If a file is moved, any alternate data stream will move along with it, as long as the destination is on an NTFS drive.
The command line can access alternate data streams using redirection operators. Streams are specified on the command line as filename:stream name.
Creating an Alternate Data Stream
As an example, a string is written into an ADS named hidden, which is associated with file test.txt:
C:\test>echo Hidden text > test.txt:hidden
The file appears to be empty, though as detailed below, the metadata is intact and associated with the file:
C:\test>dir test.txt 06/24/2010 01:33 PM 0 test.txt
Viewing an Alternate Data Stream
The metadata can be viewed by redirecting from it to more:
C:\test>more < test.txt:hidden Hidden text
The name and content of the ADS can be anything (see 'Details' below for restrictions):
C:\test>echo Arbitrary string > test.txt:arbitraryName C:\test>more < test.txt:arbitraryName Arbitrary string
Listing Files With Alternate Data Streams
On Windows Vista and later, a list of alternate data streams can be obtained using DIR /R:
C:\test>dir test.txt /R
06/24/2010 01:33 PM 0 test.txt
38 test.txt:arbitraryName:$DATA
28 test.txt:hidden:$DATA
On earlier operating systems, the SysInternals utility Streams can be used:
C:\test>c:\tools\SysInternals\streams.exe test.txt
Streams v1.56 - Enumerate alternate NTFS data streams
Copyright (C) 1999-2007 Mark Russinovich
Sysinternals - www.sysinternals.com
C:\test\test.txt:
:arbitraryName:$DATA 38
:hidden:$DATA 28
Alternate Data Streams on Directories
Metadata can be added to directories the same way it's added to files:
C:\test>mkdir test2
C:\test>echo ADS on a directory > test2:someText
C:\test>dir /r
06/25/2010 11:27 PM <DIR> .
06/25/2010 11:27 PM <DIR> ..
06/25/2010 11:27 PM <DIR> test2
42 test2:someText:$DATA
C:\test>more < test2:someText
ADS on a directory
Details
Stream Naming
To be more accurate, streams are specified as filename:stream name:stream type. It appears that the only stream type accessible from the command line is $DATA, which is why it's optional. All of the stream types are listed in the WIN32_STREAM_ID structure documentation. The default data stream is unnamed, so filename::$DATA will contain the file's data:
C:\test>echo This is the file > file.txt C:\test>echo This is the stream > file.txt:stream C:\test>more < file.txt::$DATA This is the file C:\test>more < file.txt:stream:$DATA This is the stream
Stream names are generally held to the same requirements as any filename. One interesting difference is that stream names can contain characters whose integer representations are in the range from 1 through 31. Refer to Naming Files, Paths, and Namespaces (MSDN) for details.
Note that when using streams with files having a single letter name, the filename should be prefixed with a period and backslash. The reason for this is Windows drive names. For example, does "echo hello > c:test" refer to a stream named test on file c, or does it refer to a file test on drive c?
Executing Streams
As of Windows Vista, it is no longer possible to execute directly from an alternate data stream. On Windows XP and earlier, the Start command was used, similar to start somefile.ext:hiddenExecutable.
Editing with Notepad
Notepad can be used to create and edit alternate data streams. The File Open dialog doesn't recognize stream syntax, however, so the file must be created and opened using command line parameters. Notepad will insist on appending .txt to the stream name.
Programmatic Access
Microsoft provides a sample program in C++, demonstrating how to open and write to an alternate data stream.
Real-World Applications
Downloaded Executables
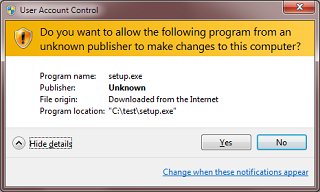
Since Windows XP SP2, when a file is downloaded from the Internet and executed (assuming a zone-aware browser), this warning is displayed:
Windows displays this warning because the web browser tagged the executable with a alternate data stream named Zone.Identifier:
C:\test>dir /r setup.exe
06/25/2010 12:10 PM 680,467 setup.exe
26 setup.exe:Zone.Identifier:$DATA
By redirecting this stream to more, we can see its contents:
C:\test>more < setup.exe:Zone.Identifier [ZoneTransfer] ZoneId=3
The PowerShell blog has more information on zone identifiers.
Viruses
The W2K.Stream virus used alternate data streams.
wow, this information its very hopefull, now i can understand how is working this part of the stream on the operating systems and i don´t knowed. And the examples are very clearly. thanks for this information.